How to protect against POODLE attacks!
Maybe you've heard about HEARTBLEED or SHELLSHOCK. POODLE is the next one.
Anyone using Windows Server and IIS was lucky enough to avoid both HEARTBLEED (openssl library vulnerability - CVE-2014-0160) and SHELLSHOCK (unix bash shell vulnerability - CVE-2014-6271). However, POODLE hits everyone.
What is POODLE?
POODLE, spelled in caps to distinguish from our furry canine friends, stands for "Padding Oracle On Downgraded Legacy Encryption". It is a type of man-in-the-middle exploit whereby an attacker can force a client connection to fallback to a vulnerable version of the HTTPS protocol, SSL v3.0. This particular type of attack is different from both HEARTBLEED and SHELLSHOCK in the sense that it is not caused by a bug in implementation, but it is a flaw in the protocol design. That means that it is unpatchable. Any type of patch would break compatibility with standard SSL v3.0 clients.
How do I protect myself against POODLE attacks?
Luckily, the vulnerable SSL v3.0 protocol has been around for ages and is now superceded by better, more robust protocols. The best way to protect your applications would be to disable vulnerable protocols, and using TLS (ideally v1.2) instead. Unless your clients are different, it is safe to disable these old protocols as most clients already support TLS. According to this study, 98.7% of clients already support TLS.
Am I vulnerable?
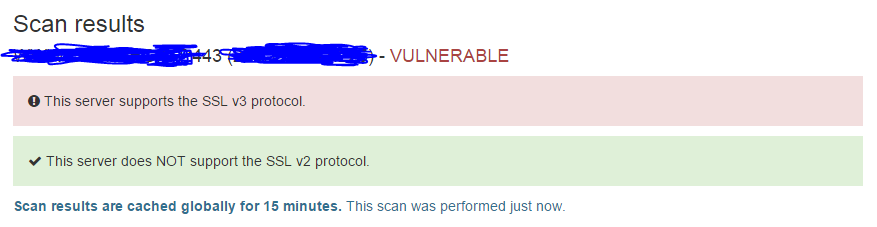
This is your first step: checking. Even if you fix it, you need to verify it, so having a reliable checking mechanism is imperative. I recommend POODLE Scan Testing tool - https://www.poodlescan.com. Drop your URL in the textbox and go. Obviously, if your app is not on HTTPS, it is not vulnerable to this particular type of attack.
If your application is private (not accessible from a public site), you can use openssl (get it from here) to attempt to connect to your service using SSL v3, like so:
openssl s_client -connect www.myserver.com:443 -ssl3
If SSL v3 is disabled, you will get the following error (ssl handshake failure).
How to disable old versions of SSL?
Once you know that SSL v2 or v3 are enabled on your server, you need to disable them. Unfortunately, there is no in-built way how to disable SSL protocols in IIS. You need to do this the old-fashioned way, through the registry.
Create a new batch file (poodle.bat) and paste the following lines to the file:
REG ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Server" /v Enabled /t REG_DWORD /d 0 /f REG ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client" /v Enabled /t REG_DWORD /d 0 /f REG ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Server" /v Enabled /t REG_DWORD /d 0 /f REG ADD "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 3.0\Client" /v Enabled /t REG_DWORD /d 0 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\DES 56/56" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 40/128" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 56/128" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC2 128/128" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128" /v Enabled /t REG_DWORD /d 00000000 /f REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128" /v Enabled /t REG_DWORD /d 00000000 /f
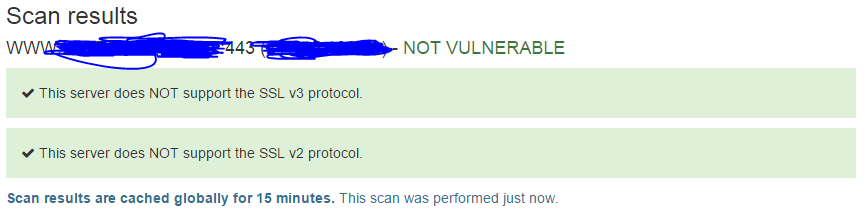
Running the above batch file on the affected server will disable obsolete weak protocols, including SSL v3. You may need to restart the server to apply the changes. Once the server is up and running again, re-check using the POODLE Scan Testing tool. Always remember to do this on your test/staging servers BEFORE applying it on your live servers!
You can also create the registry entries using powershell: http://azure.microsoft.com/blog/2014/10/19/how-to-disable-ssl-3-0-in-azure-websites-roles-and-virtual-machines/
What about Azure Paas Cloud Services?
To ensure all your Paas VMs are automatically protected, you will need to create a startup task to run the poodle.bat on every VM startup.
To do this, just grab the poodle.bat file you created earlier and add it to your Cloud Project in Visual Studio as a resource. Once done, edit the ServiceDefinition.csdef to add it as a startup task. Make sure you set the executionContext to 'elevated' for administrator access. Something like this:
<?xml version="1.0" encoding="utf-8"?> <ServiceDefinition name="myCloudService" xmlns="http://schemas.microsoft.com/ServiceHosting/2008/10/ServiceDefinition" schemaVersion="2014-06.2.4"> <WebRole name="MyWeb" vmsize="Small"> ... <Startup> <Task commandLine="..\poodle.bat" executionContext="elevated" /> </Startup> </WebRole> </ServiceDefinition>
What about Azure Web Sites?
Microsoft has promised to disable SSL v3 on all Azure Web Sites. Official quote from http://azure.microsoft.com/blog/2014/10/19/how-to-disable-ssl-3-0-in-azure-websites-roles-and-virtual-machines/
"Azure Websites will disable SSL 3.0 for all sites by default to protect our customers from the vulnerability mentioned before. We are rolling out the changes across our data-centers and monitoring traffic in the process. The changes will be rolling out through the week of Monday October 27th, 2014. Once this is complete, customers will no longer need to take any action to disable SSL 3.0 in Azure Websites and should have protection by default."
Once all this is done, POODLE would have virtually killed off SSL v3. I'm positive that it's for the best!
UPDATE 31st Oct 2014
Google plans to disable fallback to SSL 3.0 in Chrome 39, and remove SSL 3.0 completely in Chrome 40
Links
Recent Posts
-
Read More...
All Azure users, especially after the Classic-to-ARM switchover, have noticed this... There are a lot of different resource types, even for a simple deployment. Naming them becomes critical to find the appropriate resource, especially in an emergency. To make matters worse, there are a lot of similar resource types which, if you're not careful, you may end up naming the same. Need a couple of new Virtual Machines? You have to name the availability group, storage accounts, load balancer, resouce …
-
Read More...
Malta is on the map once again for the Global Azure Bootcamp, a one-day deep-dive training into the Microsoft Azure cloud.
From my last count, there will be 184 locations in total participating in this event around the world, from Hawaii to Japan! (Malta is bang in the middle!) And as usual, I'm again at it!
The bootcamp will be on April 25th 2015 (hey that's tomorrow! I suck with keeping my blog updated!) and will be held at the Microsoft Innovation Centre at Skyparks, Luqa (just …
-
Read More...
Are you using Azure Websites to host your sites? Great! Then you know that whenever you deploy a website on Azure websites, you get the mysite.azurewebsites.net URL.
The sub domain is great for you to test your application, but most probably you have your own domain that is mapped to the site. However, the azurewebsites.net domain is still there and still works! Do you know that this can be a problem?
One of the rules in the SEO bible says that each page should only have one URL. Your …
-
Read More...
A great book on the fundamentals of Azure. If you're new to Azure, this is a great start. Get it now!
The topics explored in this book include:
Getting started with Azure: Understand what cloud computing is, visit the management portals, and learn about billing.
Websites and Cloud Services: Learn about Azure Websites, from deployment to monitoring, and gain an understanding of the web and worker roles used in Azure Cloud Services.
Virtual Machines: Explore the basic …
-
Read More...
... the world shook in terror on the 19th November 2014.
That means two things: firstly, the importance of a public cloud platform such as Azure.
When such a huge thing gets a hiccup, a lot of people stress out. And they should. A lot of businesses nowadays depend on public cloud services (be it AWS or Azure), and each business trusts the availability of their service to these skilled engineers. It's true, Microsoft (or Amazon) do not own your availability promises. (You can check …
-
Read More...
Maybe you've heard about HEARTBLEED or SHELLSHOCK. POODLE is the next one.
Anyone using Windows Server and IIS was lucky enough to avoid both HEARTBLEED (openssl library vulnerability - CVE-2014-0160) and SHELLSHOCK (unix bash shell vulnerability - CVE-2014-6271). However, POODLE hits everyone.
What is POODLE?
POODLE, spelled in caps to distinguish from our furry canine friends, stands for "Padding Oracle On Downgraded Legacy Encryption". It is a type of man-in-the-middle exploit …
-
Read More...
You've published your latest masterpiece to Azure Web Sites. Great! How was it? Not bad!
Now, does your application output its own error messages (HTTP 500, 404 etc?) IIS will by default hide your errors with the message:
The resource you are looking for has been removed, had its name changed, or is temporarily unavailable.
If you want to output your own custom output for non-200 statuses, you need to put this in your web.config:
<system.webServer>
< …
-
Read More...
Building any cloud apps lately? Great!
Documenting them? Not so...
Firstly, make sure you're using the best tools of the trade: Microsoft Visio. It's by far the easiest and most powerful tool for diagrams.
Wanna add Azure-specific icons? Yeah, I know it's difficult to find them... But here's a secret: Visio supports SVG.
What does that mean, you ask? Well, it seems that the current azure site uses SVG for the majority of icons. If you want to use a particular Azure icon, just find the …
-
Read More...
How to migrate legacy apps to Windows Azure
I see a lot of interest by startups to start using Windows Azure to power their products. It's the perfect platform to start small and have room to scale quickly and easily. But the most important advantage that startups have, is not having to worry about legacy issues.
A lot of companies would like to start using the cloud. By now, we know what the advantages are: scalability, resiliency, low management overhead, low service costs, etc. …
-
Read More...
Google or Bing is indexing your public blobs on Windows Azure Blob Storage? Here is how to stop it...
The idea is to put a robots.txt file at the root of the Azure Blob Storage domain. ie: http(s)://myaccount.blob.core.windows.net/robots.txt
Follow these steps:
1. Create a new container in your storage account in question. Name it $root and allow public access to blobs. This is a special container that serves as a default container for the storage account. Any blobs in this container may …